Headless (Linux · Easy)
XSS+SUID提权
枚举
nmap
1 | nmap -sC -sT -sV - 10.10.11.8 |
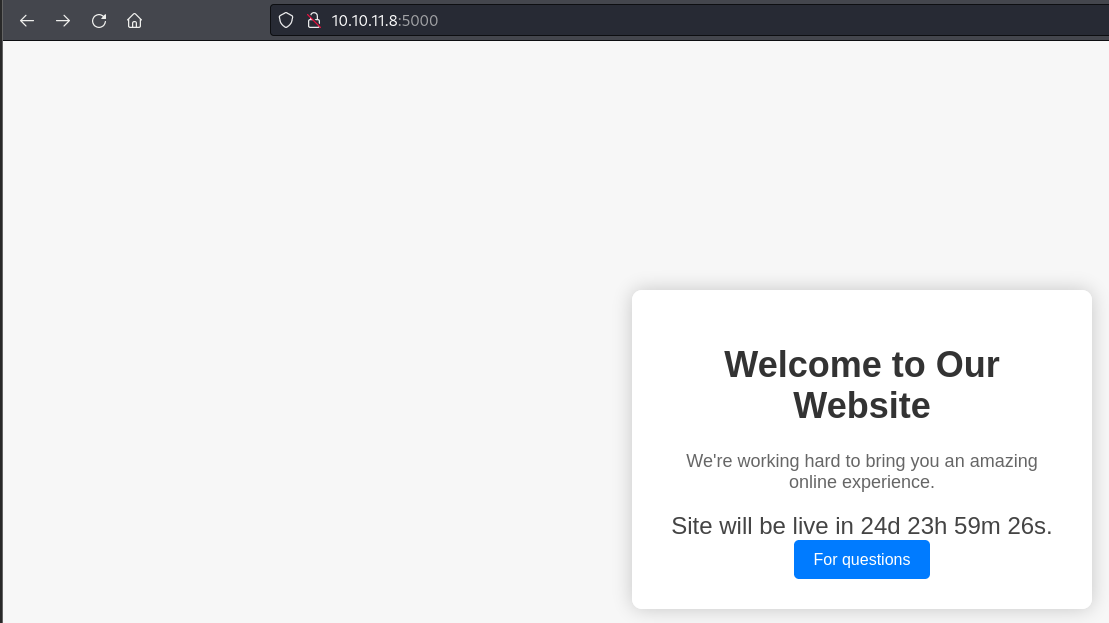
dirsearch
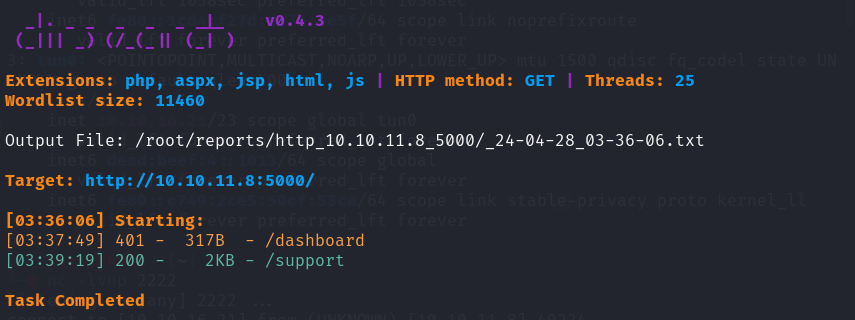
/support
XSS+SUID提权
1 | nmap -sC -sT -sV - 10.10.11.8 |


/support
fastjson于1.2.24版本后增加了反序列化白名单,而在1.2.48以前的版本中,攻击者可以利用特殊构造的json字符串绕过白名单检测,成功执行任意命令。
参考链接:
对于Fastjson来讲,并不是所有的Java对象都能被转为JSON,只有Java Bean格式的对象才能Fastjson被转为JSON。
Fastjson提供了两个主要接口来分别实现对于Java Object的序列化和反序列化操作:
JSON.toJSONStringJSON.parseObject/JSON.parse反序列化时不指定特定的类,那么Fastjson就默认将一个JSON字符串反序列化为一个JSONObject。需要注意的是,对于类中private类型的属性值,Fastjson默认不会将其序列化和反序列化。